Cybersecurity
Russian Citizen Charged for Cyber Attacks on Ukraine Prior to the 2022 Invasion
Shay M
July 3, 2024
The U.S. government has indicted Amin Timovich Stigal, a 22-year-old Russian national, for his alleged involvement in cyber-attacks against Ukraine in the lead-up to the 2022 invasion.
Stigal is accused of collaborating with the Russian military intelligence agency, called the GRU to deploy WhisperGate malware, which targets and disrupts Ukrainian government systems.
Who is Amin?
Amin Timovich Stigal ("Амин Тимович") was born on October 01, 2022, in Grozny, Chechnya, Russia.
He studied Engineering at Lyceum Maou Lyceum - the engineering center at the Republic of Tatarstan, City of Kazan, and was probably recruited by the APT group during his studies or even before.
Amin Timovich Stigal is wanted for his suspected role in cybercrimes from August 2021 to February 2022.
During this time, Stigal allegedly planned attacks on Ukraine's important computer systems.
He is accused of breaking into Ukrainian government computers, causing damage before the Russian invasion, and allegedly planned cyber-attacks on U.S. government and private systems.
On June 25, 2024, a federal arrest warrant was issued for Stigal by the United States District Court in Maryland, charging him with Conspiracy to Commit Computer Intrusion and Damage.
These attacks aimed to cause significant damage and chaos by selling stolen data on cybercrime forums in the dark and the deep web while instilling fear among the Ukrainian populace.
The U.S. Department of State is offering a substantial $10 million reward for information about Stigal’s location and supposed gang members that will lead to his arrest and conviction.
This case underscores the severe international implications of cyber warfare and highlights the ongoing efforts to bring perpetrators to justice.

WhisperGate Malware
WhisperGate is a type of destructive malware initially identified in January 2022, primarily targeting the Ukrainian government and related organizations, and has been attributed to a nation-state threat group (APT) known as "DEV-0586".
Unlike typical ransomware, which encrypts files and demands a ransom for their return, WhisperGate masquerades as ransomware but destroys data, making recovery impossible even if the ransom is paid, all designed to achieve maximum damage.
How The Malware Operates
The malware presents a fake ransom note demanding payment in Bitcoin but actually aims to destroy data rather than hold it for ransom, a thing that gives the victim a form of hope.
While it runs, the malware overwrites the Master Boot Record (MBR), rendering the system inoperable after a reboot or startup, and then corrupts files in specific directories by overwriting them.
WhisperGate has three main stages:
- The malware overwrites the MBR
- The malware executes a downloader that connects to a malicious Discord content delivery network
- It pulls and executes additional malware to corrupt targeted files
For those reasons, the main targets of WhisperGate were critical infrastructure while the idea was to undermine the public’s trust in the government.
Stigal's indictment is a crucial step in the global fight against cybercrime, emphasizing the importance of international collaboration in combating these sophisticated threats.
As cyber warfare continues to evolve, the international community remains vigilant in pursuing those responsible for these malicious acts.
This case also serves as a reminder of the broader strategy state-sponsored actors employ to destabilize nations and exert influence through digital means.
The attacks on Ukraine are part of a wider campaign to weaken governmental structures and spread disinformation.
Indicators of Compromise (IOCs) for WhisperGate Malware
WhisperGate is a destructive malware with a variety of indicators that can help in its identification and mitigation.
Below are some of the IOCs associated with WhisperGate:
File Hashes
SHA-256:
- 4ae8585b91b8ac52cb3b66bc07848e97a77d29193df24afc0e25871e103c799b
- 6fa29a226ec1c93ef3ae9f6efed2b2cfcf32a5fdc17903a5dc1e7494c8b7899e
File Names
- stage1.exe
- stage2.exe
- bootsect.bak
- config.ini
Registry Keys
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\WhisperGate
Mutexes
Global\WhisperGateMutex
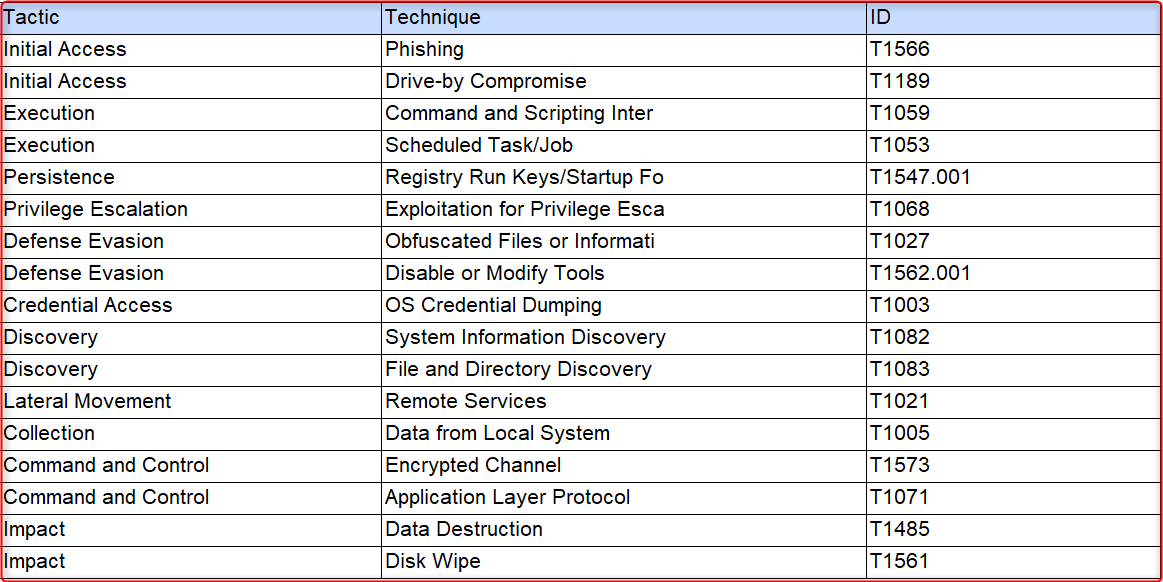
MITRE ATT&CK Techniques for WhisperGate