Background
In April 2024, a new Threat Actor, "Team ARXU” emerged.
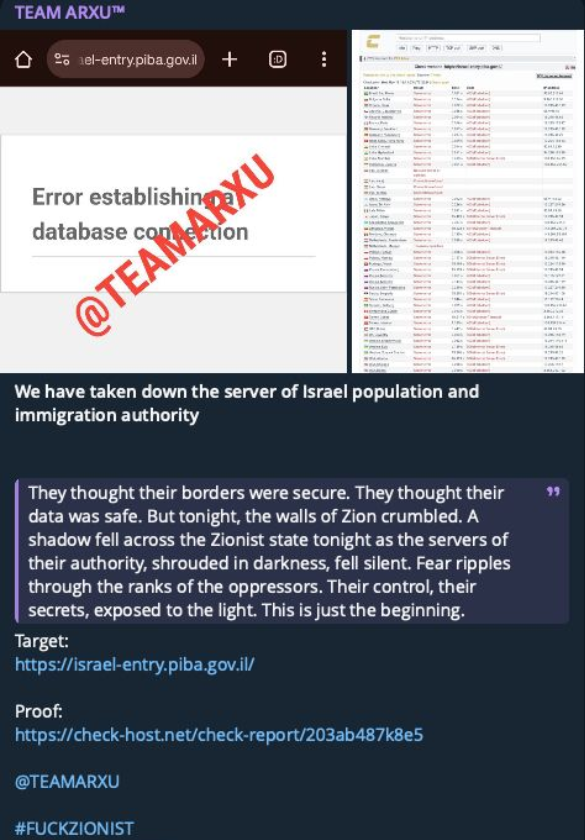
This hacktivist group from Bangladesh allegiances with the “Matryoshka 424” group. The group mainly targets Israeli infrastructure, with attacks ranging from DDoS to defacements or Data Leaks.

THE HUNT: A COMPLETE OPSEC FAILURE
The investigation began with the Telegram group @teamARXU. Searching through the group’s activity did not reveal anything unique, they share their hacks, tools, and general messages or information. We also collected another Telegram profile: @A0R3A
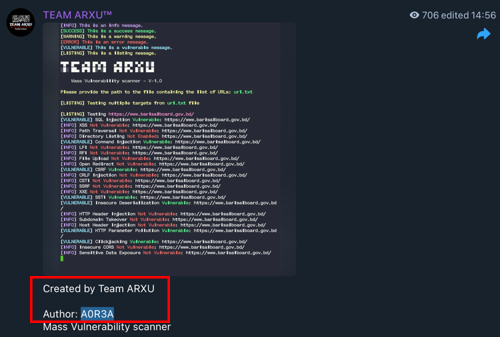
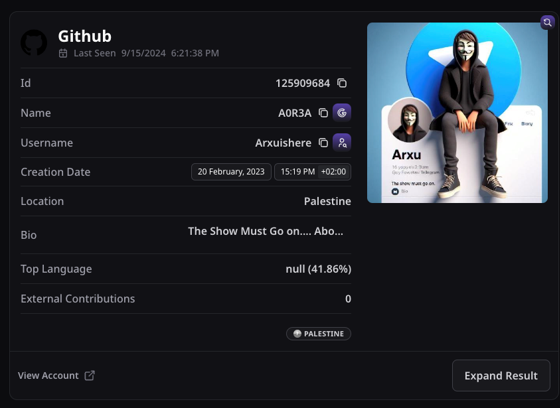
Using the username @A0R3A, and simple Dorks, our team found a GitHub profile named Arxuishere – A0R3A, claiming to be the Admin of Team ARXU. The profile is sharing all the links to their Telegram groups.
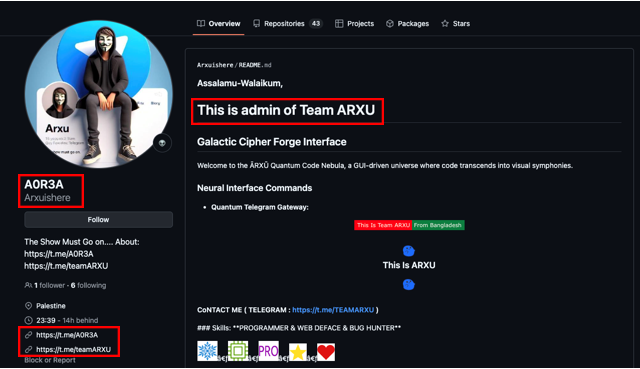
While searching the repositories did not reveal anything. However, when looking through the followers of this profile we can only observe one user following the page under the username ArafatArxu which coincidently also uses the keyword “arxu”.
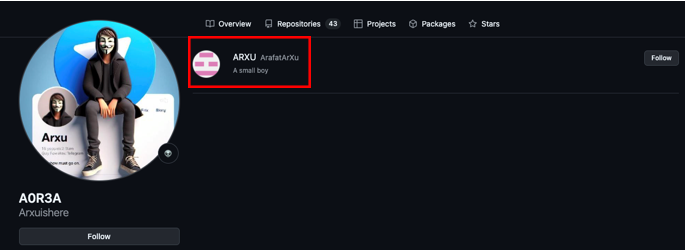
Analyzing this new profile allowed us to collect a lot of information to connect users directly to Team ARXU, such as the repositories “ARXU_BOMBER” or a link to the @A0R3A telegram group, allowing us to validate and correlate with certainty.
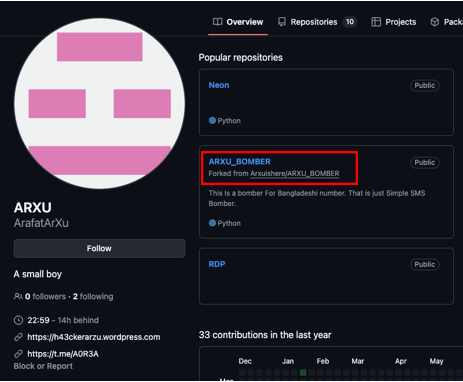
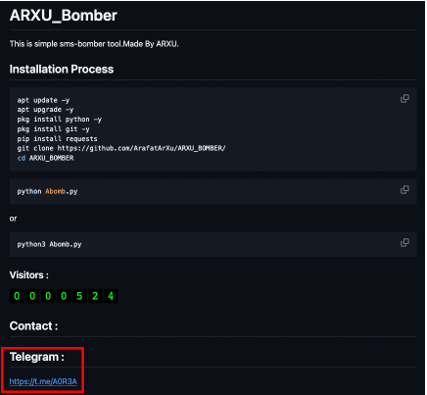
On the Bio of the GitHub profile, the user also shared a link to a WordPress domain h43ckerarzu.wordpress.com.
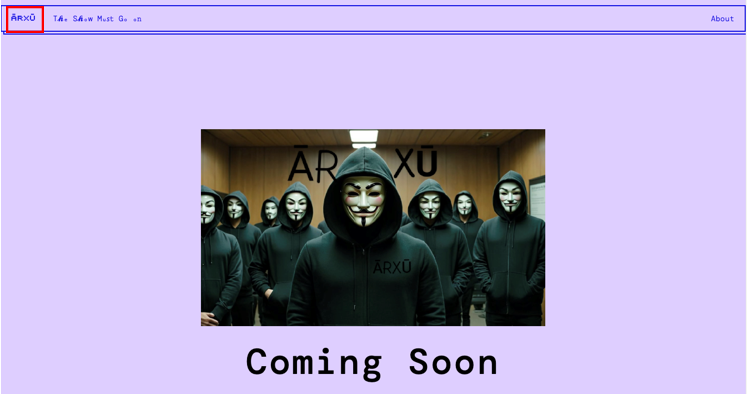
This website clearly is the early stage or version of team ARXU, simple and poorly secured. The website does not provide us with critical data apart from one single piece of information, the domain name: h43ckerarzu. This OPSEC mistake allowed us to find the individual behind the group.
Using this new identifier or potential username, we performed a simple Google Dork, which led us to a Facebook post, in a group, by a specific user, with a name that sounds familiar: Arafat Arzu.
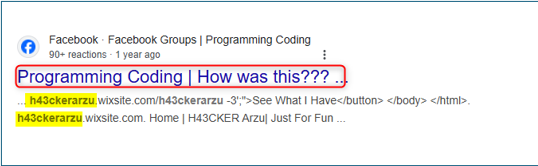
In the post, Arafat Arzu is sharing one of his defacements, where the picture shows the signature 4RXU15H3R3 aka ARXU IS HERE.
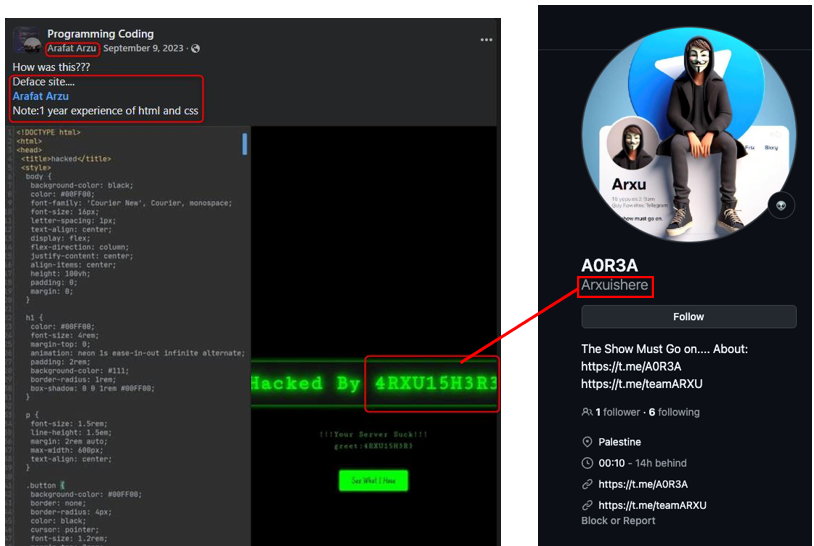
Finally, when analyzing Arafat Arzu’s profile, we get the last piece of relevant data, the username in the URL: Arafatarxu, which is the same username as on the second GitHub profile.
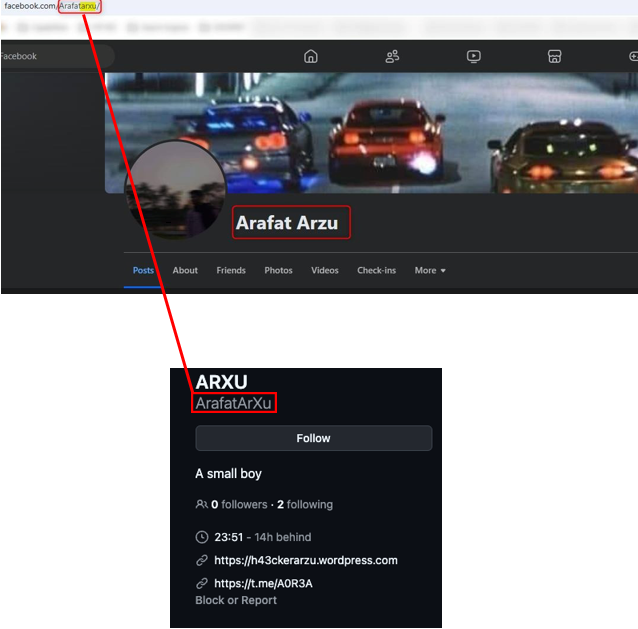
To validate and confirm the link between the Facebook profile and teamARXU, we analyzed some of the comments under the posts. In one of them, Arafat Arzu answers someone asking “send the script” by posting said script as well as a website h43ckerarzu.wixsite.com/h43ckerarzu-3.
On his website, he put a link to the @A0R3A Telegram Group.

On the website, we collected 2 emails, "4rxu@duck[.]com", and "rarafat735@proton[.]me". The last email is the critical information. This email is registered to the GitHub page "https://github.com/Arxuishere". And a Microsoft profile A0R3A Arxu.